With workplaces adapting to hybrid ways of working and BYOD arrangements, it’s critical to secure company data. Follow these intranet security best practices and embed a culture of security in your digital workplace.
In September 2022, Uber’s intranet security was compromised when a hacker targeted an Uber employee with social engineering tactics. While the story reinforced the need for robust intranet security technology, it also stands as a reminder that people are often how hackers access systems.
Despite ongoing work to secure company systems, cybersecurity continues to be a challenging area. In fact, research from 2022 suggests that cybercriminals can access 93% of enterprise networks—making cloud security critical.
If organizations hope to maintain digital workplace and intranet security, they must not only partner with vendors with comprehensive intranet security protocols, but they also need to proactively communicate security best practices with staff. It’s better to have employees embrace necessary security protocols than clear up messes created by improper, unsafe behaviors.
How to build an intranet that IT will love
What is an enterprise security culture?
Chris Romeo, CEO of Security Journey, writes:
Security culture is what happens with security when people are left to their own devices. Do they make the right choices when faced with whether to click on a link? Do they know the steps that must be performed to ensure that a new product or offering is secure?
6 ways to develop a security culture from top to bottom
A security culture is one in which every employee takes responsibility for the protection of their organization. A security culture is one where workers are empowered with the knowledge of how to guard against safety issues and the organizational support to execute such actions confidently.
How can you build a culture for optimal intranet security?
The benefits of a properly-functioning intranet security culture are clear. But, how do you arrive at that goal? Especially if your current company culture could be considered anything but secure. What systems and processes must be put in place to get all team members on board?
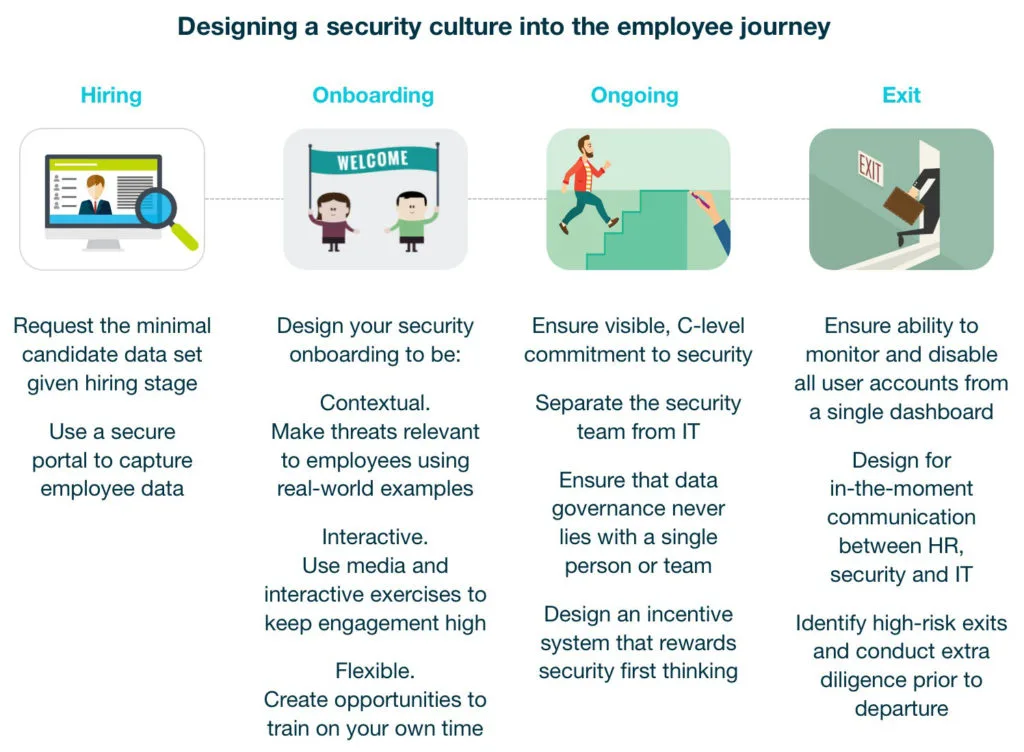
In his book, “Build a Security Culture,” Kai Roer argues that security cultures are built from three distinct components: people, policies, and technology.
These three elements give us perspectives to the world. The more we understand their formation and their continued interaction, the easier it is to understand how we can use them to build and maintain security culture.
Let’s break down each of these three elements into more practical, actionable tips for building your own culture of enterprise and intranet security.
#1 Intranet security and people
Employees are rarely malicious when it comes to security, but they may be targeted by hackers who exploit a lack of awareness.
So, while protecting your organization against coordinated attacks through advanced intranet security tools is important, it’s just as critical that the culture you build helps everyone keep company security in mind. Stopping an individual from clicking a cleverly-disguised link in a spear-phishing email may make the difference.
How to build an intranet that IT will love
Start with an assessment that answers the following questions:
- How conscious are co-workers of security issues?
- How tech-savvy are the workers at my company (this includes knowledge workers, frontline staff, remote, and others, all of whom may have different levels of access and knowledge)?
- What internal programs exist to educate them about company security protocols and their importance?
Understandably, you may have a harder time building a security culture in a company full of workers who aren’t familiar with cyberattack prevention than you might in an IT consulting firm. Knowing where you’re starting, however, will help you determine which programs or initiatives will have the biggest impact on your culture.
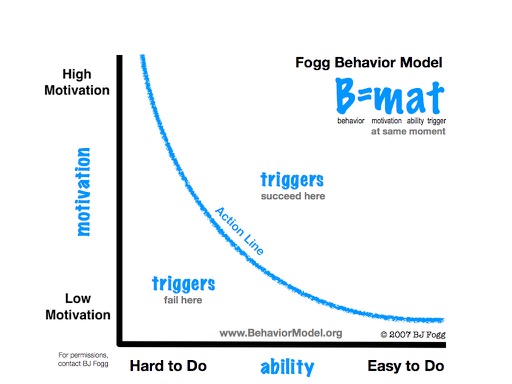
According to BJ Fogg’s Behavior Model, any attempt to nudge people to change habits must include:
- The motivation to change
- The ability to change behavior
- An awareness of triggers that dictate when behavioral change should occur
Use the results of your earlier assessment to map any training programs you develop against these criteria. If your workforce lacks technological expertise, begin with education. None of your co-workers will be able to adopt proper security measures if they don’t have the ability to understand what they are or why they’re important. This is where internal communications – coupled with line manager communications – can be exceptionally important in connecting staff with intranet security best practices.
If, on the other hand, your team is technologically aware, focus more on positive reinforcement of good behavior. Coordinate with senior leaders in your organization to develop recognition strategies that reward those who take active steps to be more secure at work. We have more ideas on driving employee adoption in our blog.
On the subject of people, it’s also worth noting that, within any organization, you’ll find employees who:
- Eagerly embrace change and the opportunity to become better workers
- Become fearful in the face of change
In these cases, you may find it helpful to identify internal influencers or security champions who have a good understanding of best intranet platform security practices, and general security awareness. These individuals may support their colleagues and evangelize the message of proper security and threat prevention across your internal comms platforms.

Give these workers a public role in a culture dedicated to maintaining intranet security. By working closely with intranet influencers and subject-matter experts, their enthusiasm will make a powerful appeal for others in your organization to adhere to best practice principles.
#2 Intranet security policies
The recognition and reward strategies mentioned above are just one of the strategies you’ll need to put in place as you build a culture capable of protecting intranet security. Having a robust series of documented policies and procedures supports the people you’re attempting to train, whether from an educational perspective (for employees who are new to security issues) or from a point of compliance (for those who understand security best practices but don’t always implement them).
Some of the specific policies you may want to put in place include:
- Documentation of internal security measures
- Role-specific standard operating procedures (SOPs)
- Codified recognition and reward strategies (or punitive measures, depending on your organization’s perspective)
At the most basic level, you need to ensure these are accessible and identifiable to employees. Having policies printed out and filed in your IT office at HQ is meaningless. Centralize the hosting of vital policies and procedures on your intranet software or DMS, and ensure they are clearly labelled and tagged for ease of search. When your employees need information, it should be readily available via the web or your mobile app.
For compliance and auditory purposes, functionality such as Mandatory Reads will enable you to track readership and remind employees of vital information they need to acknowledge.
But what about actually embedding the message rather than having employees tick a box without understanding the content?
One route you may want to consider is gamification. In an article for Security Magazine, Lance Hayden, Managing Director of Berkeley Research Group, gives the example of a friend who ran the security awareness program for a large company. In view of the organization’s lackluster approach to security, she implemented a sweeping program that made use of gamification and the socialization of security to get individual employees to take ownership for their actions.
Hayden shares:
As the awareness program grew, individuals in the organization grew more skilled in identifying signs of attack and more comfortable reporting anomalies to the security team. As a result, over time, the red team’s cost of penetration began to trend upwards as more people spotted and reported them, shutting down avenues of attack and forcing them to find new ways in.

Policies are important, but they don’t need to be sterile. Make security fun. The less employees feel burdened by the requirements of your program, the more likely they’ll be to take an active role in contributing to a culture of security.
#3 Intranet security technology
In addition to the two factors outlined above, having the right cybersecurity technology in place is crucial.
Your IT and cybersecurity experts will update technology as new threats emerge, but it is an evolving picture and not one that is ever “done”. For that reason, communicators should remain engaged in a dialogue with IT and alive to the need to communicate changes regularly with employees.
As Mike Saurbaugh, a faculty member with IANS Research, a course developer for Excelsior College and an independent consultant, suggests in an interview with Security Intelligence:
Developing a comprehensive security awareness program should not be considered a destination, but a journey. It requires dedicated oversight and should be ongoing, with engaging exercises.

Continually commit to improving your security culture, and measure the impact of your changes not just in numerical metrics but in patterns that suggest security behaviors are being implemented and embraced by employees.



